Idempotency Strategies for Modern Payment Systems.
Because “Retry” Should Never Mean “Double Charge”
In payment systems, failure is normal.
Networks timeout. Clients retry. Mobile apps resend requests. Load balancers duplicate traffic.
If your API is not idempotent, retries can turn into double charges, inconsistent ledgers, and customer trust issues.
In this article, we’ll break down:
- What idempotency really mean
- Why payments demand it
- How to design an idempotent payment API in Java
- Production patterns that actually work
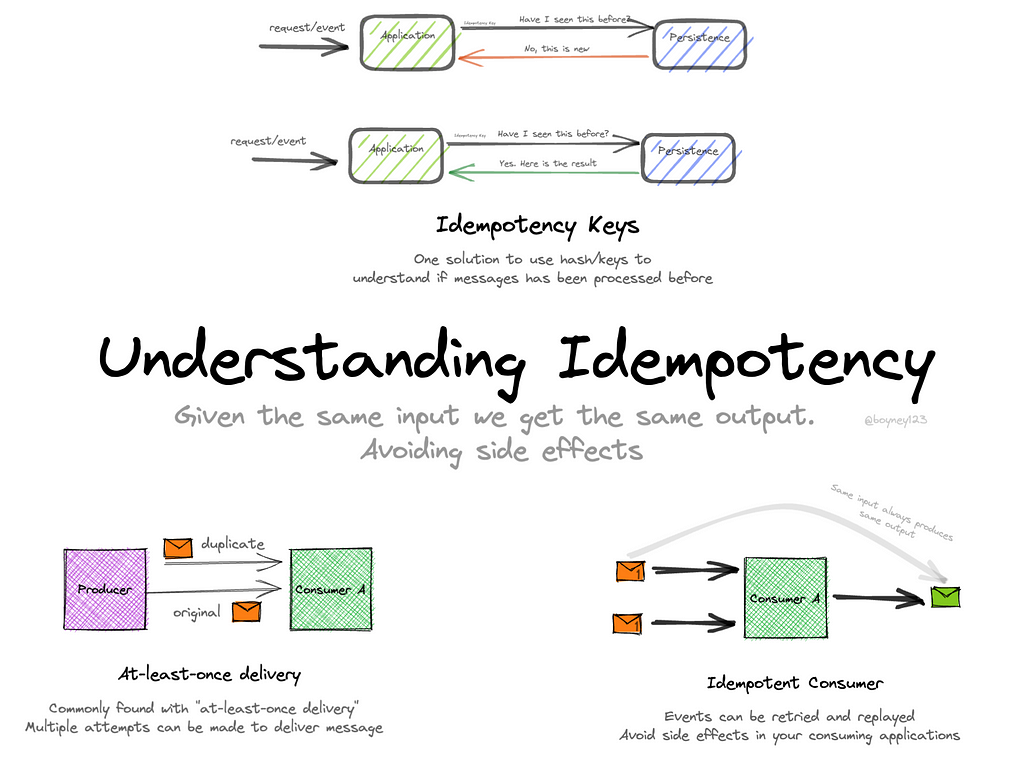
What Is Idempotency (Really)?
An operation is idempotent if performing it multiple times produces the same result as performing it once.
For payments:
If a client sends the same payment request 5 times due to a timeout,
→ only one transaction should be processed.
All retries must return the same response.
Core concepts & contract
HTTP request
POST /payments
Headers:
Idempotency-Key: 8f3d9a1c-2234-4aaf-b3a2-91fa01fbb321
Content-Type: application/json
{
"amount": 2500,
"currency": "KES",
"sourceAccount": "acct_123",
"destinationAccount": "acct_456",
"metadata": { "merchantOrderId": "order_987" }
}
Server guarantees
- If a request with the same Idempotency-Key and same request body is received multiple times → the server returns the same response (status + body) each time and performs the payment flow once.
- If the same Idempotency-Key is used with a different body → server returns 409 Conflict (possible fraud/misuse).
- If first attempt is in-flight and another identical request arrives concurrently → server ensures only one executes.
Step-by-Step Design in Java (Spring Boot Example)
1. Create an Idempotency Table
CREATE TABLE idempotency_keys (
id BIGSERIAL PRIMARY KEY,
idempotency_key VARCHAR(255) UNIQUE NOT NULL,
request_hash CHAR(64) NOT NULL,
response_body TEXT,
status_code INT,
created_at TIMESTAMP WITH TIME ZONE DEFAULT now(),
updated_at TIMESTAMP WITH TIME ZONE DEFAULT now()
);
CREATE INDEX idx_idempotency_created_at ON idempotency_keys(created_at);
Notes
- request_hash = SHA-256 of the canonicalized request body (and possibly important headers).
- response_body stores the serialized JSON response that was returned for the first successful attempt.
- Add TTL cleanup job: remove records older than retention window (24–90 hours typical depending on retries / legal needs).
Basic server flow (Spring Boot pseudocode)
- Read Idempotency-Key header → validate presence and format.
- Compute requestHash = sha256(canonicalizedRequestBody).
- Try to insert an idempotency_keys row with key + requestHash (no response yet):
a. If insert succeeds → process payment, save response, and return response.
b. If insert fails due to duplicate key → fetch record and:
- if record.requestHash != requestHash → return 409 Conflict.
- if record.response_body set → return stored response (replay).
- if record.response_body not set → wait / poll briefly and return current status or 409 depending on policy.
Example Java snippets (high-level):
@RestController
public class PaymentController {
@PostMapping("/payments")
public ResponseEntity<String> createPayment(@RequestHeader("Idempotency-Key") String key,
@RequestBody PaymentRequest req) {
String reqHash = sha256(canonicalize(req));
Optional<IdempotencyRecord> existing = repo.findByKey(key);
if (existing.isPresent()) {
IdempotencyRecord r = existing.get();
if (!r.getRequestHash().equals(reqHash)) {
return ResponseEntity.status(HttpStatus.CONFLICT).body("Idempotency key reuse with different payload");
}
if (r.getResponseBody() != null) {
return ResponseEntity.status(r.getStatusCode()).body(r.getResponseBody());
}
// In-flight: could return 202 Accepted or wait/poll briefly
return ResponseEntity.status(HttpStatus.ACCEPTED).body("Request is being processed");
}
try {
// Attempt insert as atomic guard
repo.insert(new IdempotencyRecord(key, reqHash));
} catch (DataIntegrityViolationException e) {
// Someone else inserted concurrently; fetch and replay
IdempotencyRecord r = repo.findByKey(key).get();
if (!r.getRequestHash().equals(reqHash)) {
return ResponseEntity.status(HttpStatus.CONFLICT).body("Idempotency key reuse with different payload");
}
if (r.getResponseBody() != null) {
return ResponseEntity.status(r.getStatusCode()).body(r.getResponseBody());
}
return ResponseEntity.status(HttpStatus.ACCEPTED).body("Request is being processed");
}
// Now process payment inside transaction
PaymentResponse resp = paymentService.process(req);
// Save response to idempotency table
repo.updateResponse(key, resp.getStatus(), serialize(resp));
return ResponseEntity.status(resp.getStatus()).body(serialize(resp));
}
}
Concurrency guard patterns, why unique index + upsert wins
Options:
- SELECT … FOR UPDATE: locks a row, works but you must create a row first or use a sentinel row.
- Unique constraint + insert-then-catch-duplicate: simple, scales, and leverages database atomicity.
- Advisory locks (Postgres): fine for some workloads but be careful with lock lifetime on failures.
Recommendation: use unique constraint as primary guard. It’s simple, transactional, and reliable.
2. Fast-path: Redis for high QPS
If your API handles thousands of requests per second and you want low-latency idempotency checks:
- On incoming request:
- SETNX idemp:{key} “{request_hash}” EX 300 (or use a small TTL)
- If SETNX returns true → this process will handle the request. Proceed and persist to DB.
- If SETNX returns false → read the DB (or Redis value) and respond accordingly.
Caveats
- Redis-based guard is a cache — DB must be the source of truth. Always persist to DB as soon as possible.
- Redis eviction or restart can lose entries → rely on DB fallback.
- Ensure atomicity for the fast-path + DB write: write-through pattern or use Redis to prevent duplicate work but always persist.
Hashing & canonicalization: don’t get tricked
- Canonicalize the request before hashing (ordering keys, normalize numeric formats, exclude non-deterministic fields like timestamps unless they are part of the contract).
- Use SHA-256 of canonical JSON. Example:
MessageDigest digest = MessageDigest.getInstance("SHA-256");
byte[] hash = digest.digest(canonicalJson.getBytes(StandardCharsets.UTF_8));
String hex = Hex.encodeHexString(hash);
Store that hex as request_hash in DB.
Handling partial failures & downstream idempotency
A common nightmare: your payment processor returns success, but saving the idempotency row or ledger entry fails. Now the charge occurred, but your system believes it didn’t.
Strategies:
- Two-phase approach with durable inbox or outbox
- Write intent + ledger entry to DB first (as part of the same transaction), then publish to the external payment processor from a durable outbox.
- Outbox guarantees delivery and lets you retry without double processing.
2. Make downstream writes idempotent
- Ledger writes must be keyed by transactionId or paymentId and implemented with upserts / INSERT … ON CONFLICT DO NOTHING.
- This ensures that retried processing won’t create duplicate ledger rows
3. Compensation & reconciliation
- Implement a reconciliation job: compare external payment provider transactions with internal ledger; create compensating entries or refunds when mismatches are found.
- Keep robust audit logs and timestamps.
4. Store external provider response identifiers
- Store providerTransactionId with idempotency record to reconcile and dedupe.
Status codes and response replay
- If initial attempt succeeded → return 201 Created (or 200 OK) and store that full response (headers, status, body). Replays must return the same status.
- If payload mismatch with same key → 409 Conflict.
- If the initial request is still being processed and the server can’t return final result immediately → 202 Accepted with a status endpoint for the client to poll.
- Avoid returning 500 for idempotent replays; once successful, responses must be stable.
Security & anti-abuse
- Limit idempotency key length and character set.
- Rate-limit keys per client to avoid key exhaustion attacks.
- Authenticate and authorize the request: idempotency keys are scoped to client identity (token + key). A key from client A must not affect client B.
- Encrypt sensitive parts of stored request/response or avoid storing raw PII.
Retention, GDPR and TTL policies
- You don’t need to store idempotency keys forever. Typical ranges:
- Short-lived payments: 24–72 hours
- Long-running flows or asynchronous payments: up to 30 days
- Implement a background cleanup job to delete old idempotency rows.
- Consider legal / audit requirements (e.g., regulated financial records might require longer retention for certain fields — consult compliance).
Observability & metrics
Track:
- idempotency.requests.total — total requests with Idempotency-Key
- idempotency.replays — how many replays served
- idempotency.conflicts — key collisions with different payloads
- idempotency.latency — time to check/insert the record
- idempotency.insert_failures — DB uniqueness or transaction failures
Also log: idempotency_key, request_hash, payment_id, provider_txn_id (avoid logging raw PII).
Testing checklist
- Unit tests: hashing canonicalization, mismatch detection.
- Integration tests: concurrent requests with same key — ensure only one payment occurs.
- Chaos testing: simulate DB fail after provider success → verify outbox/reconciliation recovers correctly.
- Load testing: measure Redis fast-path vs DB-only approach.
- Security tests: key reuse by different clients, rate limits.
Example: Kafka + consumer idempotency (event-driven payment flow)
If your system is event-driven:
- Producer publishes PaymentRequested with idempotencyKey.
- Consumer must dedupe before processing:
- Use idempotency table or Kafka compacted topic keyed by idempotencyKey.
- Consumer should perform INSERT idempotency_keys … before ledger write. If duplicate, skip processing.
This ensures eventual consistency with exactly-once effect at the ledger level.
Conclusion: Idempotency Is a Trust Guarantee
In payment systems, failure is inevitable. Networks will drop. Clients will retry. Messages will duplicate. Concurrency will happen.
The real question is not if duplicates occur, it’s whether your system is designed to handle them safely.
Idempotency is not just an implementation detail or a header in an HTTP request. It is a deliberate architectural decision. It requires:
- A durable persistence layer
- Concurrency control at the database level
- Deterministic request hashing
- Idempotent downstream ledger writes
- Clear operational monitoring and reconciliation
When implemented correctly, idempotency transforms unreliable networks into reliable financial workflows. It ensures that retries do not translate into double charges, inconsistent ledgers, or lost trust.
Exactly-once processing may be a theoretical ideal in distributed systems. Idempotency, however, is practical, enforceable, and production-proven.
In financial engineering, trust is the product.
And idempotency is one of the core mechanisms that protects it.
About the Author
William Achuchi
Backend Engineer & System Architect
Java | Spring Boot | .NET | Modular Monoliths | Microservices
Portfolio: williamachuchi.com
X (Twitter): @dev_williee
I build enterprise-grade backends, highly modular systems, and clean architecture platforms.
Open to collaborations, backend engineering roles, architecture reviews, and open-source work.
Idempotency Strategies for Modern Payment Systems. was originally published in Javarevisited on Medium, where people are continuing the conversation by highlighting and responding to this story.
This post first appeared on Read More

